1、拓扑和需求
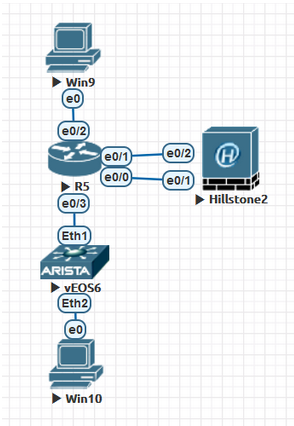
win10(172.16.1.2/24)访问win10(192.168.1.2/24),正常流量通过防火墙进行访问控制,当防火墙宕机可以通过交换机直接互相访问。
2、配置步骤
(1)防火墙配置:
rule id 1
action permit
src-addr “Any”
dst-addr “Any”
service “Any”
exit //这里先放通所有策略,实际情况根据需求放通策略interface ethernet0/1
zone “trust”
ip address 20.20.20.2 255.255.255.0
manage ping
exit
interface ethernet0/2
zone “untrust”
ip address 10.10.10.2 255.255.255.0
manage ping
exit //接口配置
ip vrouter “trust-vr”
ip route 0.0.0.0/0 10.10.10.1
ip route 192.168.1.0/24 20.20.20.1
exit //路由配置
(2)核心交换机配置:
interface Ethernet0/0
ip vrf forwarding B
ip address 20.20.20.1 255.255.255.0
!
interface Ethernet0/1
ip vrf forwarding A
ip address 10.10.10.1 255.255.255.0
!
interface Ethernet0/2
ip vrf forwarding A
ip address 172.16.1.1 255.255.255.0
!
interface Ethernet0/3
ip vrf forwarding B
ip address 192.168.1.1 255.255.255.0
! //接口配置,把不同的接口划分到不同的VRF中ip route vrf A 192.168.1.0 255.255.255.0 10.10.10.2
ip route vrf B 0.0.0.0 0.0.0.0 20.20.20.2//路由配置,指向防火墙的路由
ip vrf A
rd 1:1
route-target export 1:1
route-target import 1:1
route-target import 2:2
!
ip vrf B
rd 2:2
route-target export 2:2
route-target import 1:1
route-target import 2:2//vrf配置,选择性的导入导出路由
router bgp 1
!
address-family ipv4 vrf A
redistribute connected
!
address-family ipv4 vrf B
redistribute connected
! //bgp配置,把直连路由分别重分布给VRF A和VRF B
不能配置两条静态路由在vrf之间发布每个前缀,因为这种方法不被支持——报文不会被路由器路由。为了实现vrf之间的路由泄漏,必须使用route-target的import功能,并在路由器上启用BGP (Border Gateway Protocol)协议。不需要BGP邻居。
3、说明
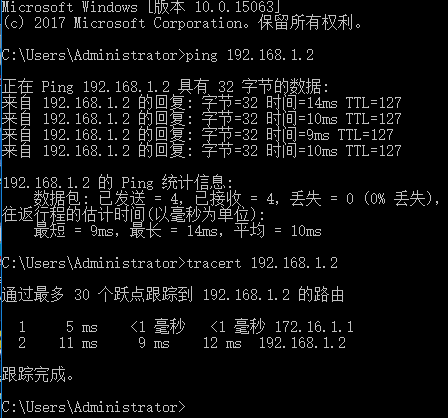
(1)正常流量通过防火墙进行访问控制;
防火墙运行正常时:
显示所有通过bgp学习到的vpnv4前缀:
Router#show ip bgp vpnv4 all
% BGP cannot run because the router-id is not configuredBGP table version is 9, local router ID is 0.0.0.0
Status codes: s suppressed, d damped, h history, * valid, > best, i – internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
Origin codes: i – IGP, e – EGP, ? – incomplete
RPKI validation codes: V valid, I invalid, N Not foundNetwork Next Hop Metric LocPrf Weight Path
Route Distinguisher: 1:1 (default for vrf A)
*> 10.10.10.0/24 0.0.0.0 0 32768 ?
*> 20.20.20.0/24 0.0.0.0 0 32768 ?
*> 172.16.1.0/24 0.0.0.0 0 32768 ?
r> 192.168.1.0 0.0.0.0 0 32768 ?
Route Distinguisher: 2:2 (default for vrf B)
*> 10.10.10.0/24 0.0.0.0 0 32768 ?
*> 20.20.20.0/24 0.0.0.0 0 32768 ?
*> 172.16.1.0/24 0.0.0.0 0 32768 ?
*> 192.168.1.0 0.0.0.0 0 32768 ?
Router#
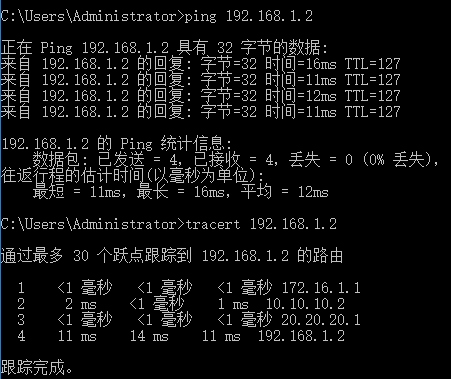
(2)当防火墙宕机,shutdown核心R5的e0/0 和e0/1接口模拟防火墙宕机,流量直接通过核心,不影响客户业务。
防火墙宕机时:
Router#show ip bgp vpnv4 all
% BGP cannot run because the router-id is not configuredBGP table version is 13, local router ID is 0.0.0.0
Status codes: s suppressed, d damped, h history, * valid, > best, i – internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
Origin codes: i – IGP, e – EGP, ? – incomplete
RPKI validation codes: V valid, I invalid, N Not foundNetwork Next Hop Metric LocPrf Weight Path
Route Distinguisher: 1:1 (default for vrf A)
*> 172.16.1.0/24 0.0.0.0 0 32768 ?
*> 192.168.1.0 0.0.0.0 0 32768 ?
Route Distinguisher: 2:2 (default for vrf B)
*> 172.16.1.0/24 0.0.0.0 0 32768 ?
*> 192.168.1.0 0.0.0.0 0 32768 ?
Router#






 私信站长
私信站长
没有回复内容